Full solution of Investigation challenge from InCTFi 2020.
tl;dr
- Extract process last run time from the windows registry.
- Extract process run count from the windows registry.
Challenge points: 100
No. of solves: 117
Challenge Author: stuxn3t
Challenge description
You can download the file from here: Google Drive.
Initial analysis
We are provided with a Windows memory dump. I’ll be using Volatility to analyze, extract relevant artefacts.
Finding the profile
We shall use the imageinfo plugin to find the profile of the memory dump
$ volatility -f windows.vmem imageinfo
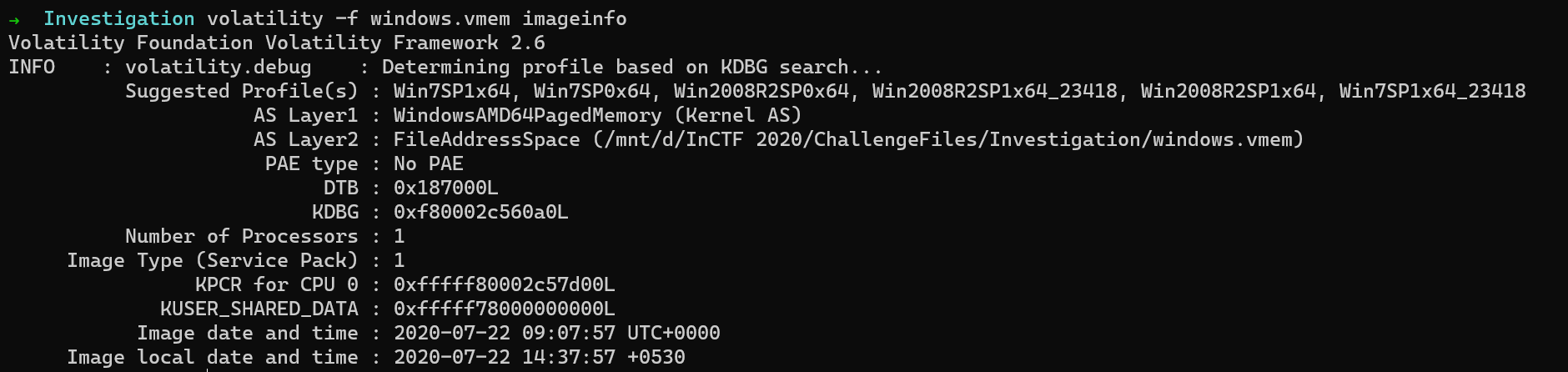
So let us use the profile as Win7SP1x64.
Answering 1st question
Question 1: When did Adam last use the Windows calculator? {:.info} So to find out when the calculator was last run, let us first try pslist, because if calc.exe was running in the system, then we can easily get the time stamp directly from the output generated by the pslist plugin.
$ volatility -f windows.vmem --profile=Win7SP1x64 pslist
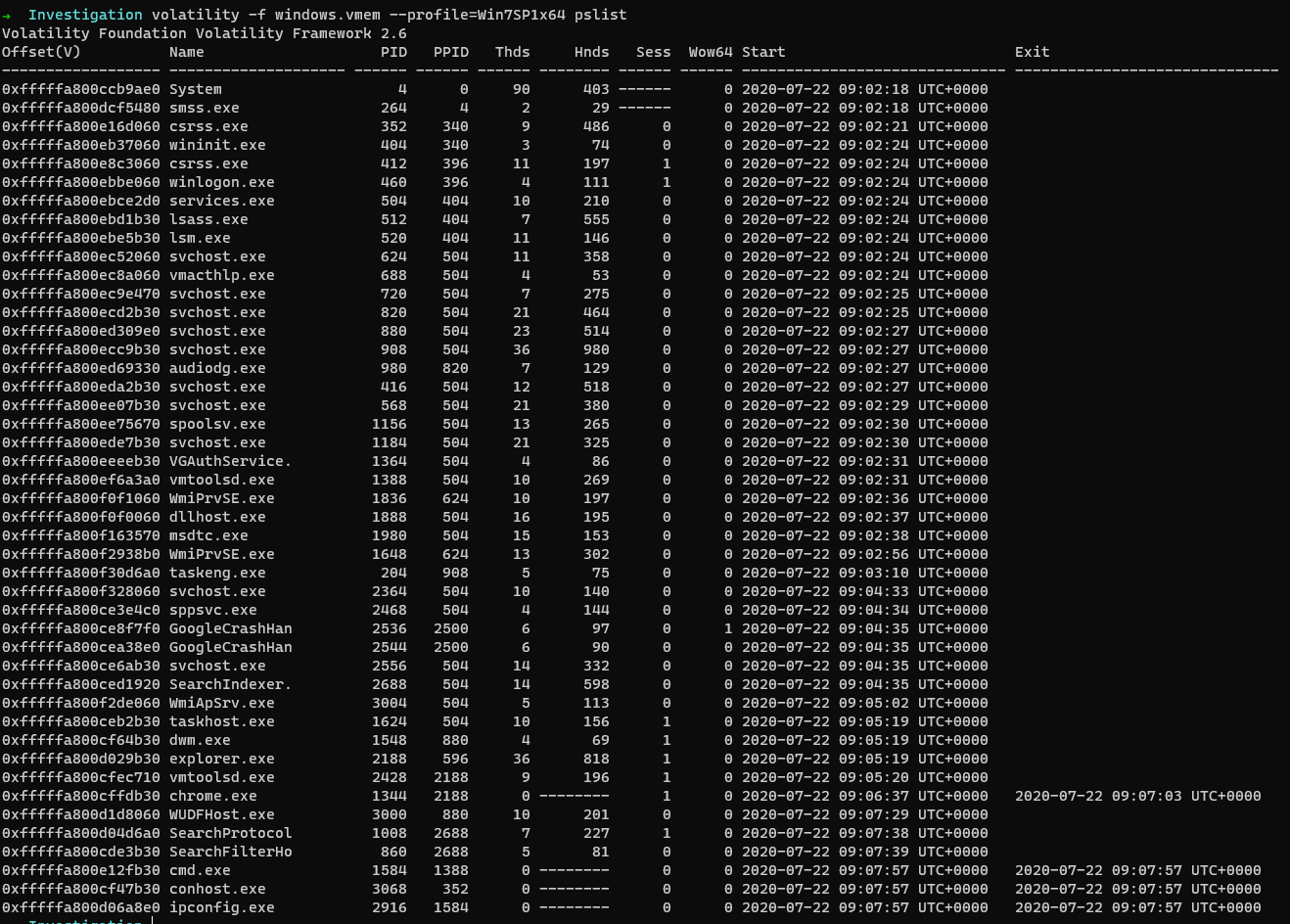
Well, we do not find any trace of calc.exe being executed. However, we do have a different source to obtain all the evidence we need. That is the Windows Registry.
The windows registry is a very very rich source of information. It has so many details that a forensic examiner needs to extract its information.
The details of processes like run count, Last run time, execution path etc… can be found in the Windows registry. To list out the registry hives, we can use the hivelist plugin.
$ volatility -f windows.vmem --profile=Win7SP1x64 hivelist
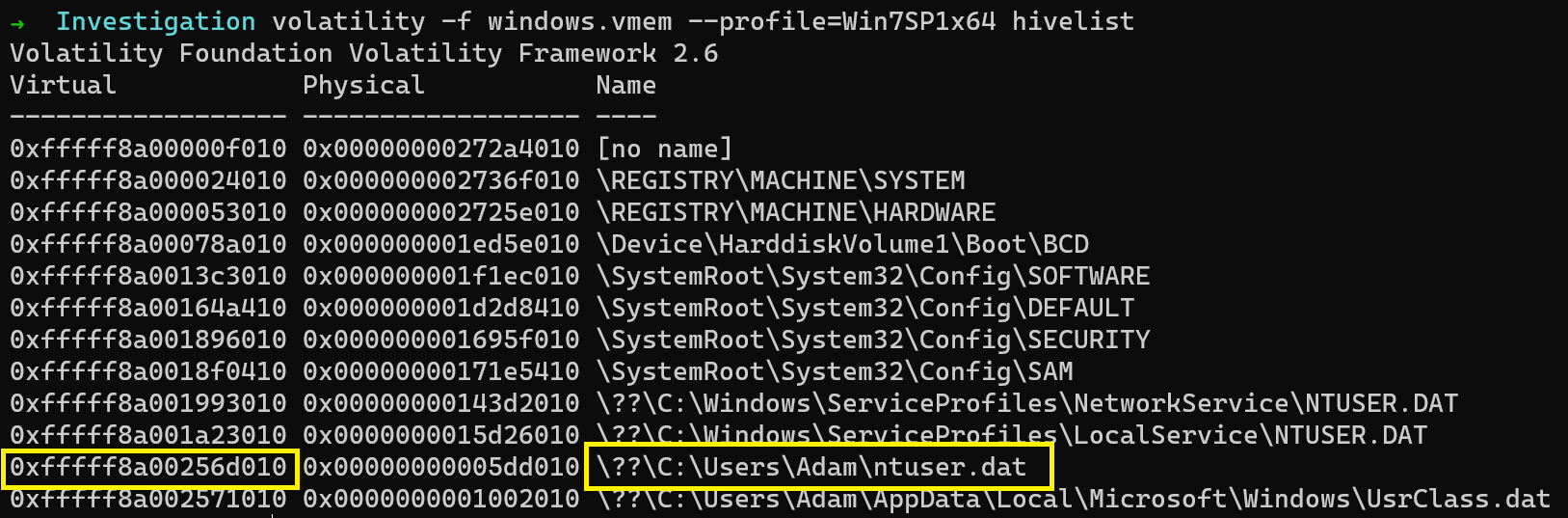
The important hive for this challenge is the NTUSER.DAT. So let me dump the hive and proceed to analyze its contents.
$ volatility -f windows.vmem --profile=Win7SP1x64 dumpregistry -o 0xfffff8a00256d010 -D .
I will be using Eric Zimmerman’s Registry Explorer to load and analyze the registry.
PATH: Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count {:.info}
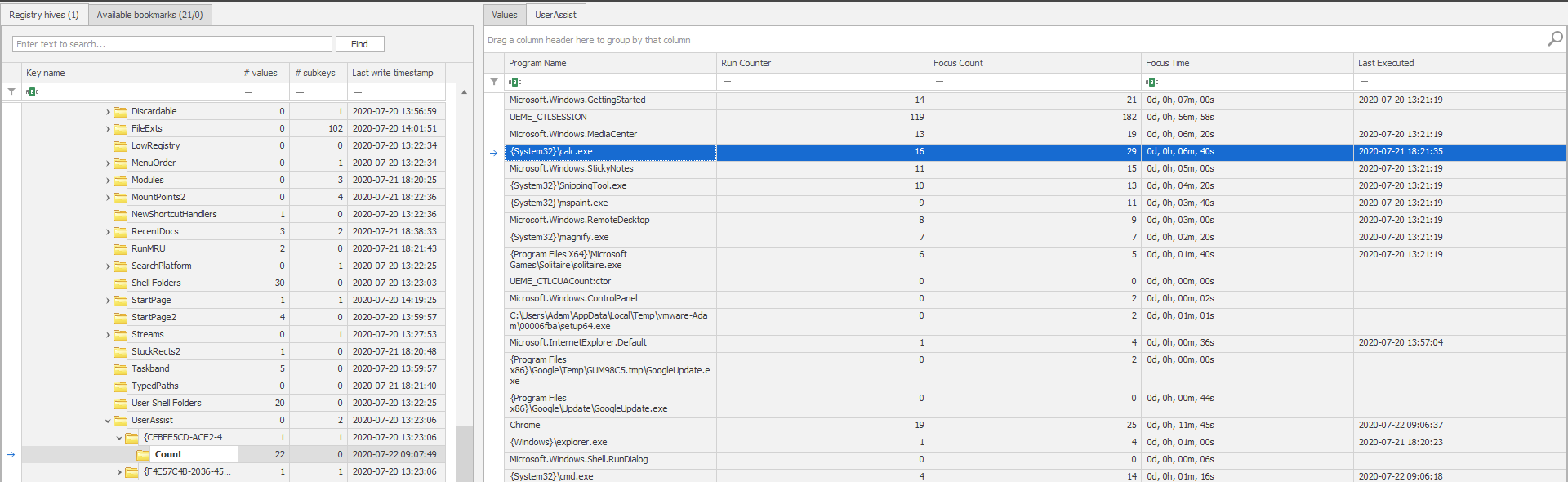
As highlighted, the last run time of calc.exe is 2020-07-21 18:21:35. Converting that to the format mentioned in the description would result in 21-07-2020_18:21:35.
Answering 2nd question
In the same registry, we can also find the number of time Google Chrome was executed on the system.
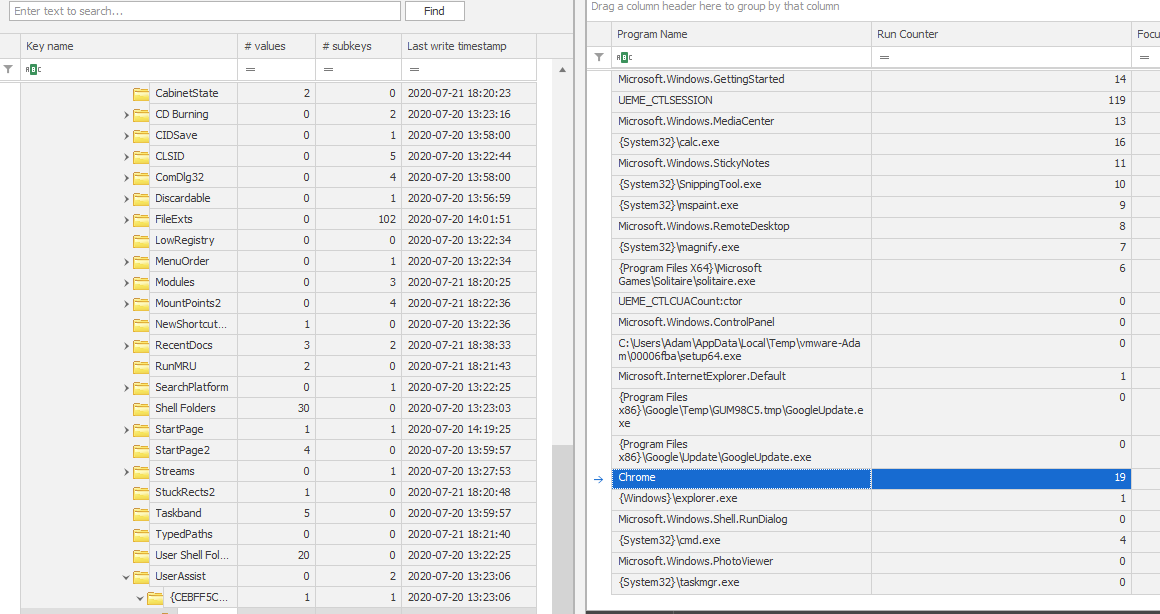
As highlighted, the number is 19.
Flag
Let us concatenate the two answers as mentioned.
FLAG: inctf{21-07-2020_18:21:35_19} {:.success}
For further queries, please DM me on Twitter: https://twitter.com/_abhiramkumar
References
- Registry Explorer
- Volatility command reference