Full solution of Notch It Up challenge from InCTF Internationals 2019.
tl;dr
- Chrome history analysis
- File recovery from the memory dump
- Raw analysis of email content
- Environment variables analysis
- RAR password cracking
- Corrupted file analysis
Challenge points: 900
No. of solves: 11
Challenge Authors: stuxn3t, Sh4d0w & g4rud4
Challenge Description
You can download the challenge file at MEGA or G-Drive
Writeup
We are provided with a Windows 7 memory dump. Let us begin our initial level of analysis.
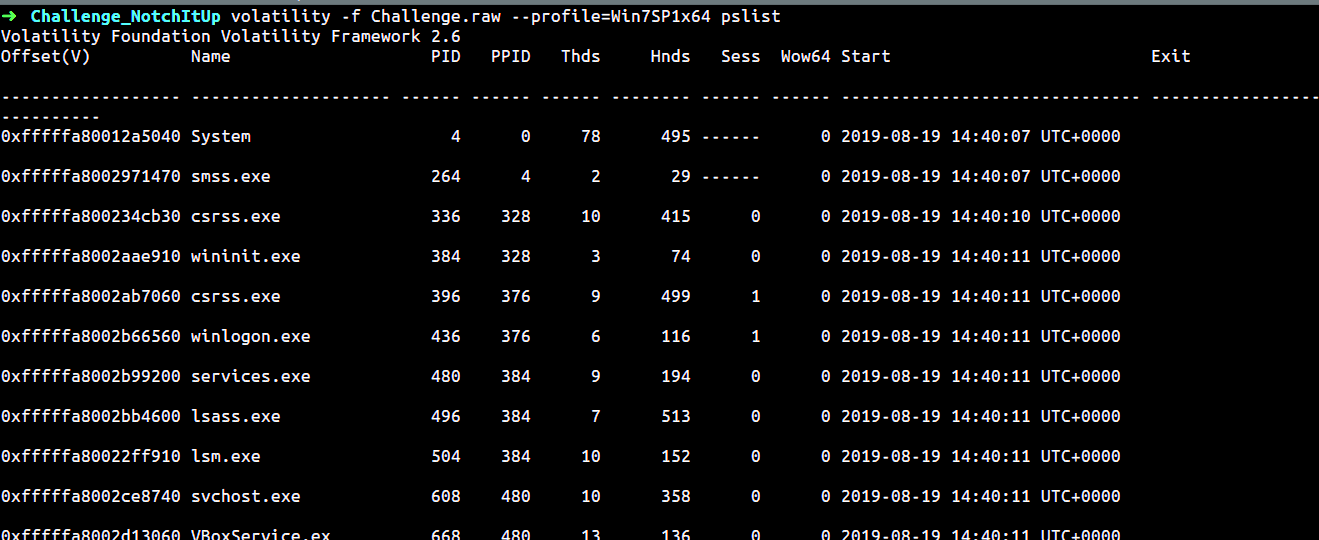
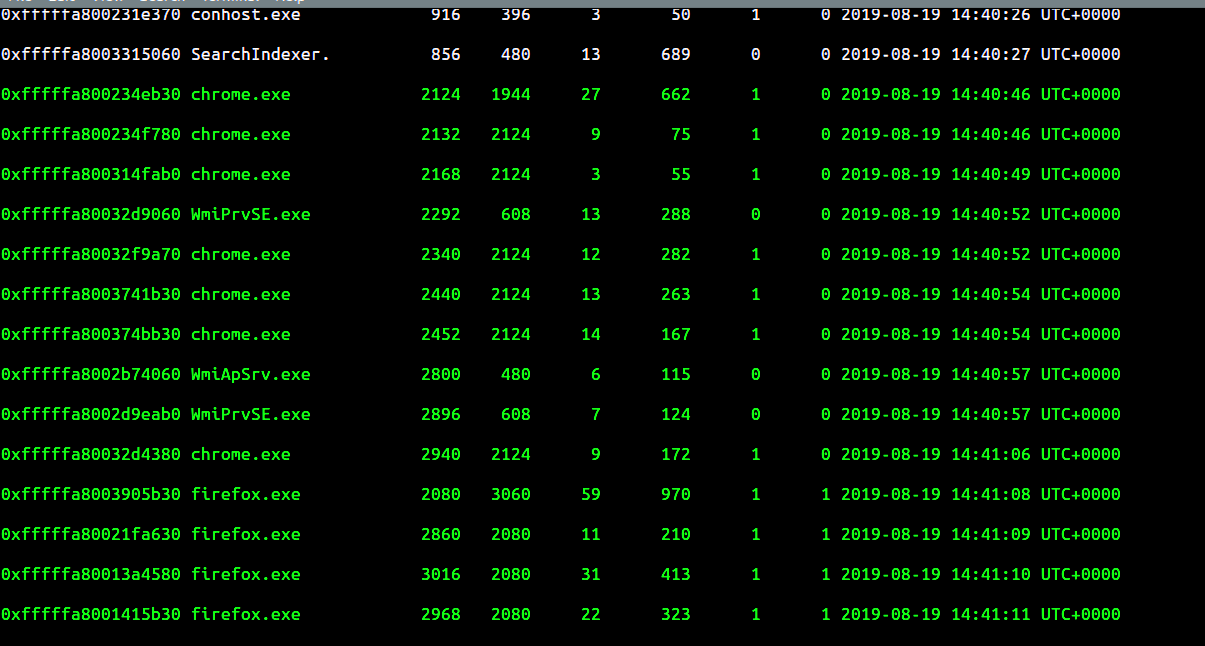
Let’s start with the running processes.
$ volatility -f Challenge.raw --profile=Win7SP1x64 pslist
Retrieving browser history
As seen above, we see chrome and firefox as active running processes. Let us see the history of google chrome here. I have trimmed most of the content and only focussing on the relevant part of the history
$ volatility --plugins=volatility-plugins/ -f Challenge.raw --profile=Win7SP1x64 chromehistory
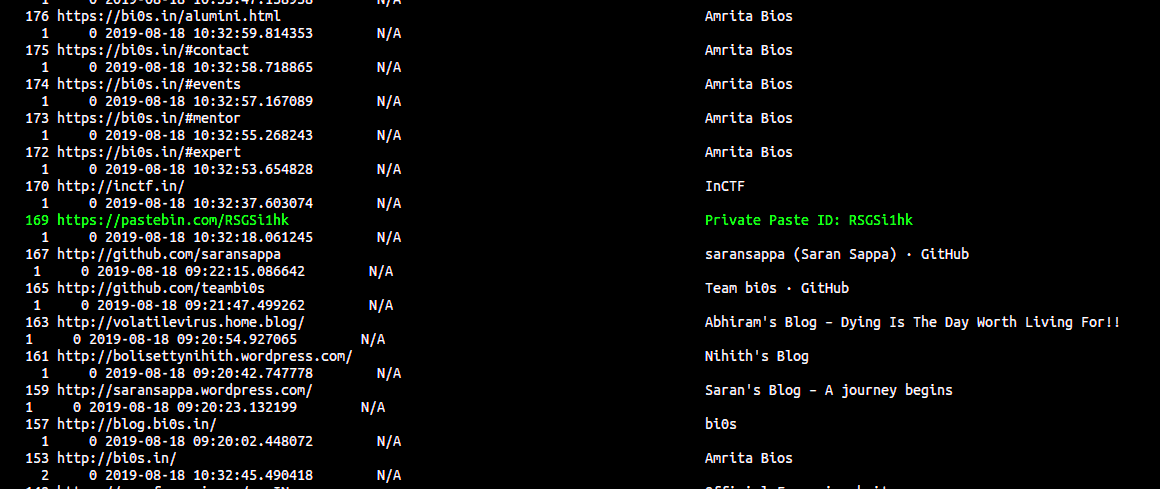
Hmm, we find an interesting PasteBin link. The link is: https://pastebin.com/RSGSi1hk
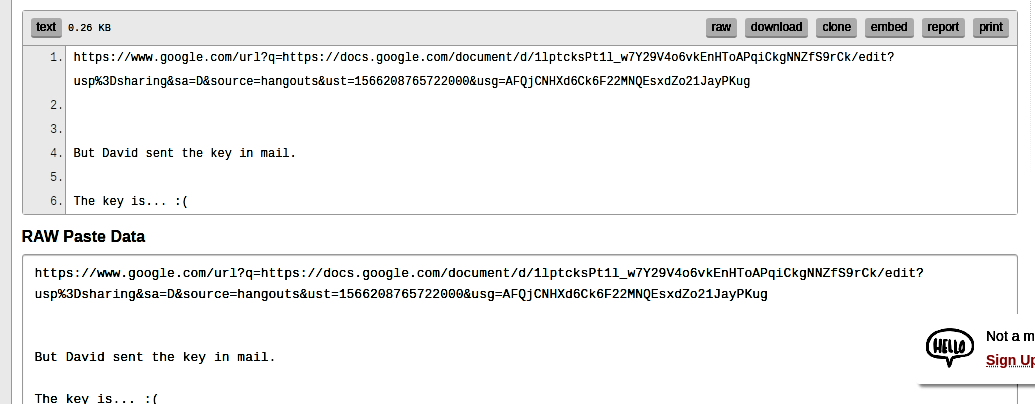
The Pastebin link contains another Google Docs link, lets head there. The docs link is: click here
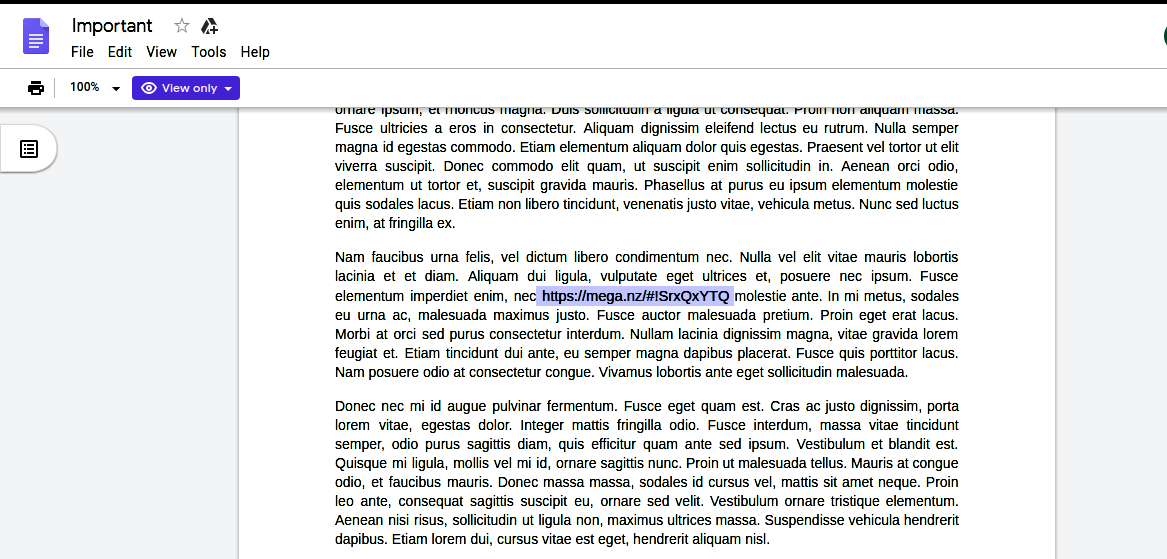
The doc contains a lot of spam but we find one interesting link which leads us to a mega drive: https://mega.nz/#!SrxQxYTQ.
However, to download the file present in the mega drive, we need to find the KEY. However, the text in the Pastebin link tells us that “David sent the key in mail”.
Retrieving screenshots of PC
Okay, let me use the Screenshot plugin. Maybe it’ll help.
$ volatility -f Challenge.raw --profile=Win7SP1x64 screenshot -D .

We see that the browser window is open and also that GMail is open with the subject Mega Drive Key. Now it is the time to begin a little raw analysis. So a small intro. The data, when loaded into ram, is not encrypted, so basically, whatever you type in the browser window or load in it is saved as a sort of JSON data. So we just have to locate some JSON sort of data which contains our subject string “Mega Drive Key”. Let us see if we can get the email data.
So what I did was use the command strings. Simple.
$ strings Challenge.raw | grep "Mega Drive Key"
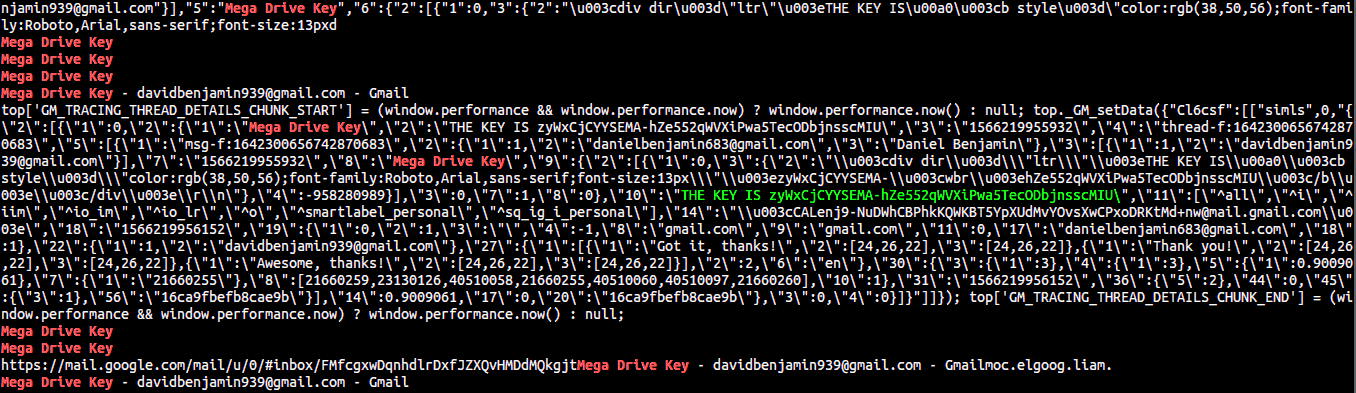
So the key is zyWxCjCYYSEMA-hZe552qWVXiPwa5TecODbjnsscMIU.
So we find a PNG image in the drive. However, PNG is corrupted. Fixing the IHDR of the image gives us the 1st part of the flag.
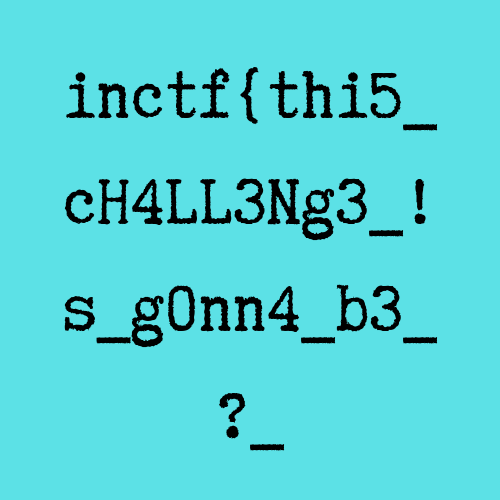
The first part is: inctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_ {:.success}
Finding the other half
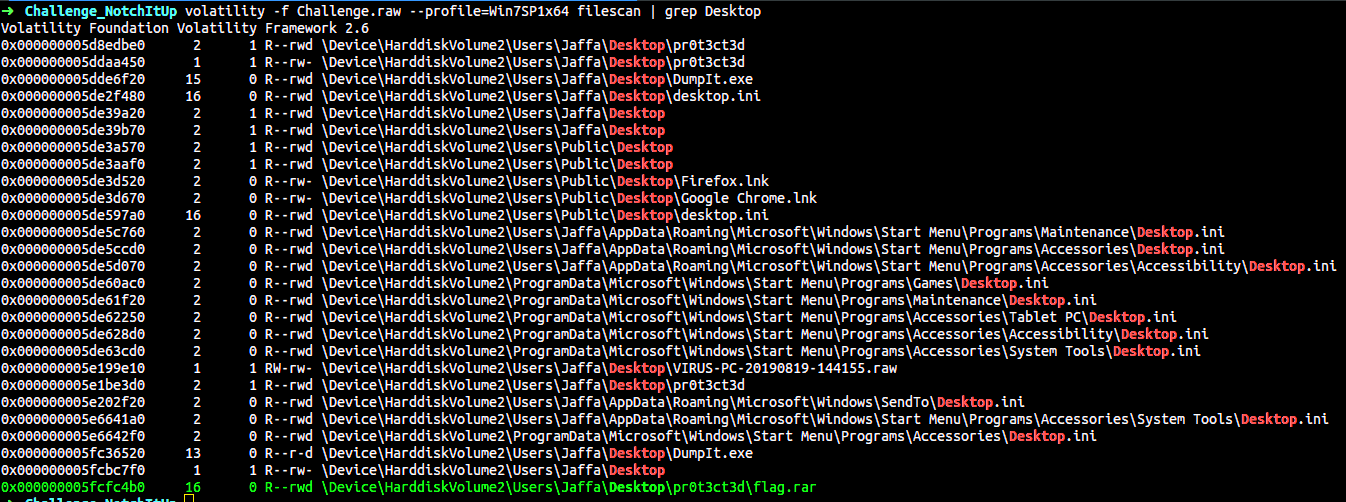
Now moving onto the second part, Let us use the filescan plugin to find what kind of open-files are present in the system.
$ volatility -f Challenge.raw --profile=Win7SP1x64 filescan | grep Desktop
In the desktop of the system, we see a folder by the name pr0t3ct3d. It contains a RAR archive with the name flag.rar
Let us dump the RAR archive with the help of the dumpfiles plugin.
$ volatility -f Challenge.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000005fcfc4b0 -D .
However, the archive is password protected. Also, brute-forcing for the password is not at all intended. So let us look for some other clues which may help us to get the password of the archive.
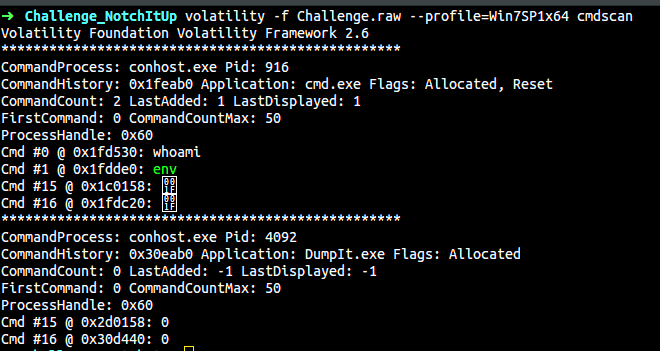
Using the cmdscan plugin, we see that env command has been used but that is an invalid command in windows command prompt. So let us look at the state of the Environment variables.
$ volatility -f Challenge.raw --profile=Win7SP1x64 cmdscan
$ volatility -f Challenge.raw --profile=Win7SP1x64 envars
We observe a custom variable created named RAR password.
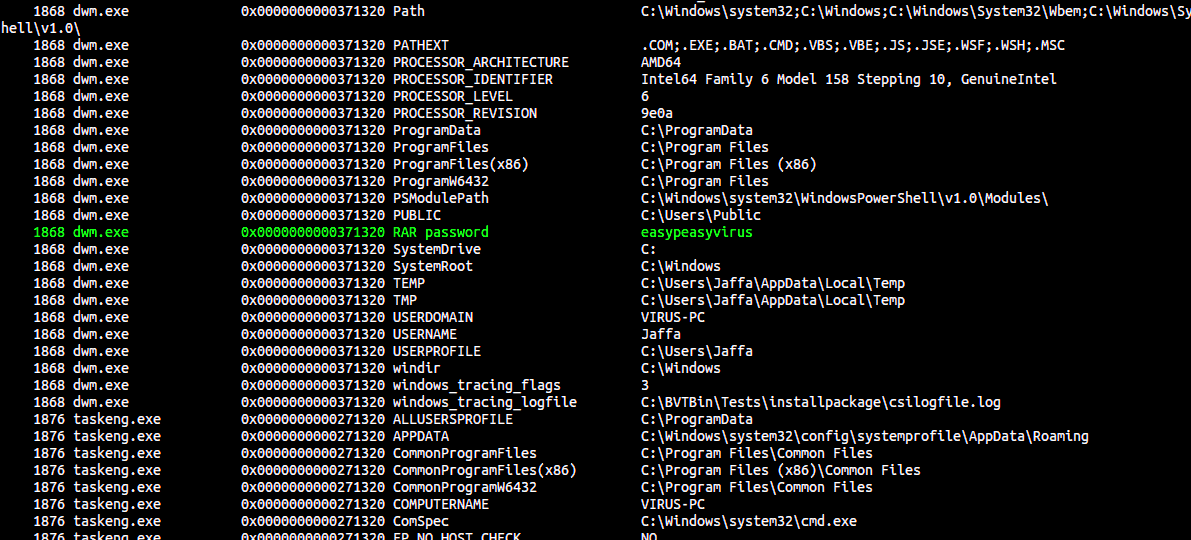
So it gives out the password as easypeasyvirus. Now we get the last part of the flag.

So now let us concatenate the 2 parts to finish off the challenge.
Flag
FLAG: inctf{thi5_cH4LL3Ng3_!s_g0nn4_b3_?_aN_Am4zINg_!_i_gU3Ss???_} {:.success}