Full solution of RR challenge from HackTM CTF Quals 2020.
tl;dr
- RAID recovery
- JPEG image extraction from lost disk
Challenge points: 298
No. of solves: 67
Solved by: stuxn3t
Challenge Description
The challenge file can be downloaded from Google-Drive or Mega-Drive.
Initial Analysis
When I downloaded the files, I observed that one of the images had no data in it. Also, the description provides us with information that one of the drives was lost. So I obviously concluded that the challenge involved RAID recovery.
The concept of RAID recovery is quite simple. You can simply obtain/recover the lost drive by xoring the others and rebuilding the RAID files might give me the flag. So let us get into it.
XORing the images
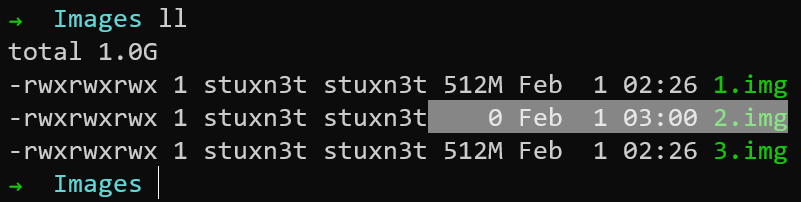
As you can see in the image below, the drive 2.img has been lost. So we have to XOR 1.img and 3.img to recover the original image.
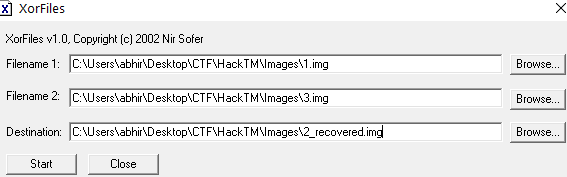
For this, I used a simple tool called XorFiles
Using this tool, I Xor-ed 1.img, 3.img and obtained the new file.
Carving out the JPEG
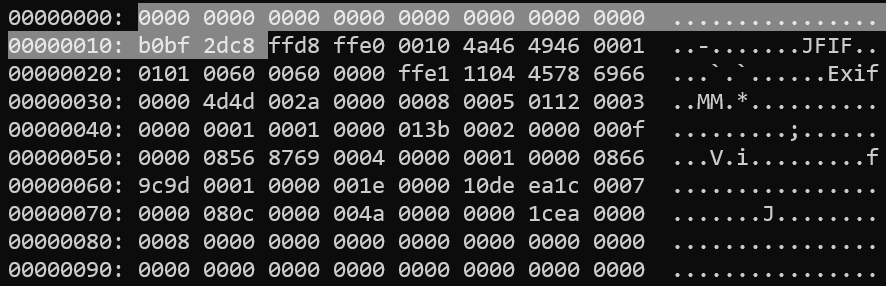
I initially thought of rebuilding the whole image, mounting it and then accessing the flag. However, I did not do that. I observed the hexdump of the file and found a JPEG image header.

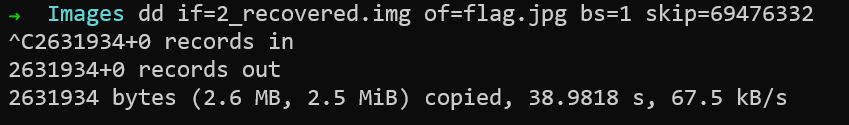
So I knew just what to do. I simply used dd to carve out the file from the offset.
$ dd if=new.img of=flag.jpg skip=69476332 {:.info}
Well, the offset I used had some extra bytes at the start so we can simply remove till we get the start of the valid JPEG file signature.
Flag
After deleting the extra bytes at the start and opening the new image in any image viewer gives us the flag
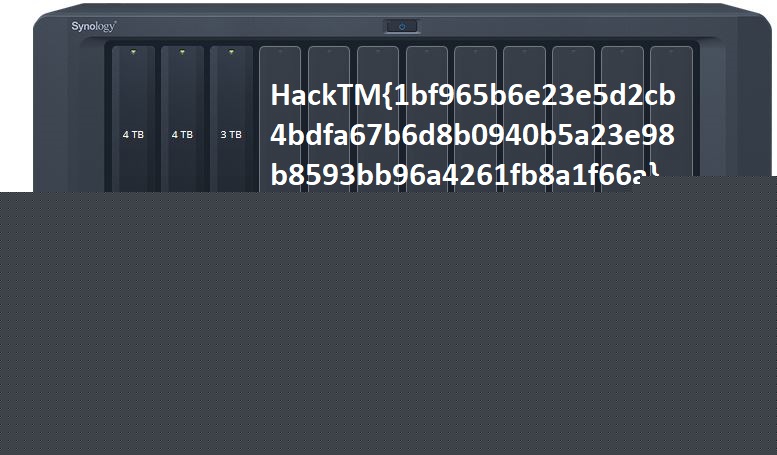
FLAG: HackTM{1bf965b6e23e5d2cb4bdfa67b6d8b0940b5a23e98b8593bb96a4261fb8a1f66a} {:.success}
For further queries, feel free to message me on Twitter: https://twitter.com/_abhiramkumar